How Managed It Services Jacksonville can Save You Time, Stress, and Money.

The service provider will alert you of growths in the IT industry that could be helpful to your service as well as provide you the option to transform the services you are getting. You might likewise have the ability to consist of some software-as-a-service (Saa, S) subscriptions that would certainly be beneficial to your business. This permits you to prevent keeping programs and associated data locally, therefore releasing up area and boosting security.
It Managed Services Jacksonville for Beginners
This permits you to pay on an as-needed basis instead than spend a collection amount monthly. It can be an excellent alternative for services who would certainly like to prevent long-term contracts. Particularly, there are some sorts of IT solutions that it makes more feeling to outsource as needed.
You can additionally use equipment services to eliminate out-of-date devices. A professional will take care of your equipment properly, that includes format hard drives to wipe them of all details just deleting data is ineffective and presents a safety and security risk. When you outsource software services, the provider will see to it that your licenses are constantly current as well as that your business is adhering to end-user arrangements.
For circumstances, the company can locate licenses that you're still paying for however not utilizing. Network solutions start with the configuration of framework at your area, consisting of setting up servers, setting up firewall programs, and also attaching printers. The company might likewise apply safety and security actions to avoid unauthorized logins and also to apply two-factor verification.
The 6-Second Trick For Jacksonville It Consulting
Chatbots An IT carrier can create a chatbot for your company. This will permit you to connect with customers who see your website or message you on social networks while getting rid of the demand for a real-time conversation representative. Relying on your target market, customers might favor to interact with a chatbot than to call or email.
You can minimize the demand for this service by giving employees with adequate training on the tools they need to make use of. The most crucial IT service of all is cybersecurity. Whereas a number of the above solutions cover cybersecurity to some level, if you are at specific risk from an assault (such as if your business deals with delicate info), it's worthwhile obtaining this solution from a specialist.
Indicators on It Services Jacksonville You Should Know
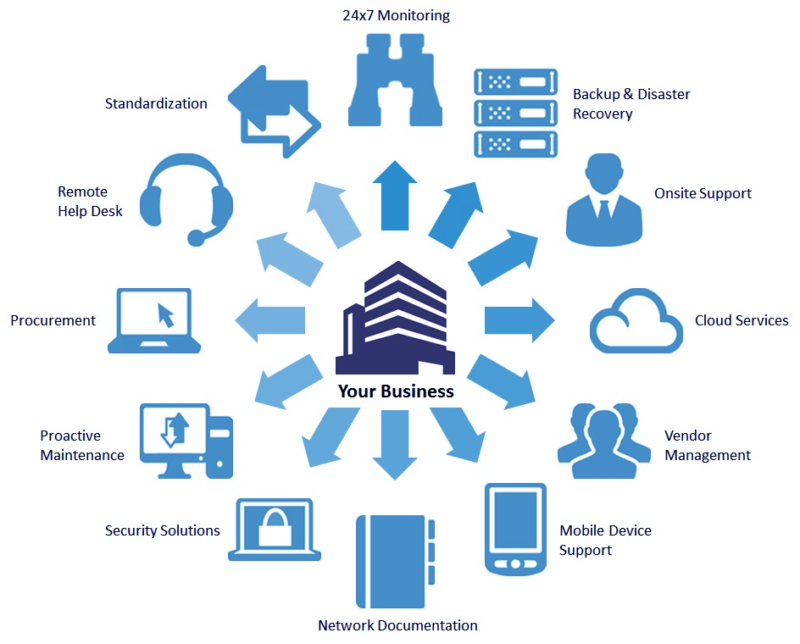
Numerous little companies pick this choice, as it makes it less complicated to get a range of solutions from one area. You may determine it would certainly be much better to contract out some certain solutions as well as agreement Get More Info others simply when you need them. Making a decision which sorts of IT solutions you might such as outsource is just the beginning.
As foresaid, IT sustain offers end-to-end managed IT services, which include article source these mainly: An IT infrastructure has a variety of laptops, workstations, printers, servers and equipment systems - network support jacksonville. A small damage or failure may finish up in a great loss, which might be of essential information or information. This occurring inevitably influences on the company's returns and also continuity.
See This Report about Jacksonville Tech Support
The tech engineers prepare qualifications to verify tools as well as records to preserve this system correctly. The entire operations goes on while accepting end-user contracts. Besides that, this assistance supplies cost-reduction. The expertly experienced designers find cost-efficient alternatives to replace with pricey applications that are barely made use of as well as their permit is soon to be expired.
Furthermore, these experts monitor the network, invasions as well as web traffic night and day. Whatever that is done comes under its specified network policies. These policies have multi-factor authentication, stopping out of the state logins and numerous other ones in a great duty. This is incredibly for the firms that permit staff members to use their very own phones for carrying out jobs.
Excitement About It Consulting Jacksonville
This occurring does not require any kind of direct energetic management by the individual. There are large clouds, which usually obtain dispersed over several locations. As its advantages are outstanding, an increasing number of companies have begun shifting to the cloud for holding their information. For keeping their secret information concerning clients and also their client experience (CX) risk-free, it comes with some phenomenal protection attributes.
The assistance team keeps an eye on the network and also brings out circumstances administration technique to maintain it up with the strict security procedures. This is a critical and also core practice which specifies the dexterity of any kind of IT sustain. It is additionally worth keeping in mind that a technical assistance solution can likewise be organized to service the business's employees within the company, for example, if employees require technological assistance with computer devices (a computer/printer has broken down) or non-working software.